Cooperative Two-Factor Authorisation: Multiple Approvals Allowed
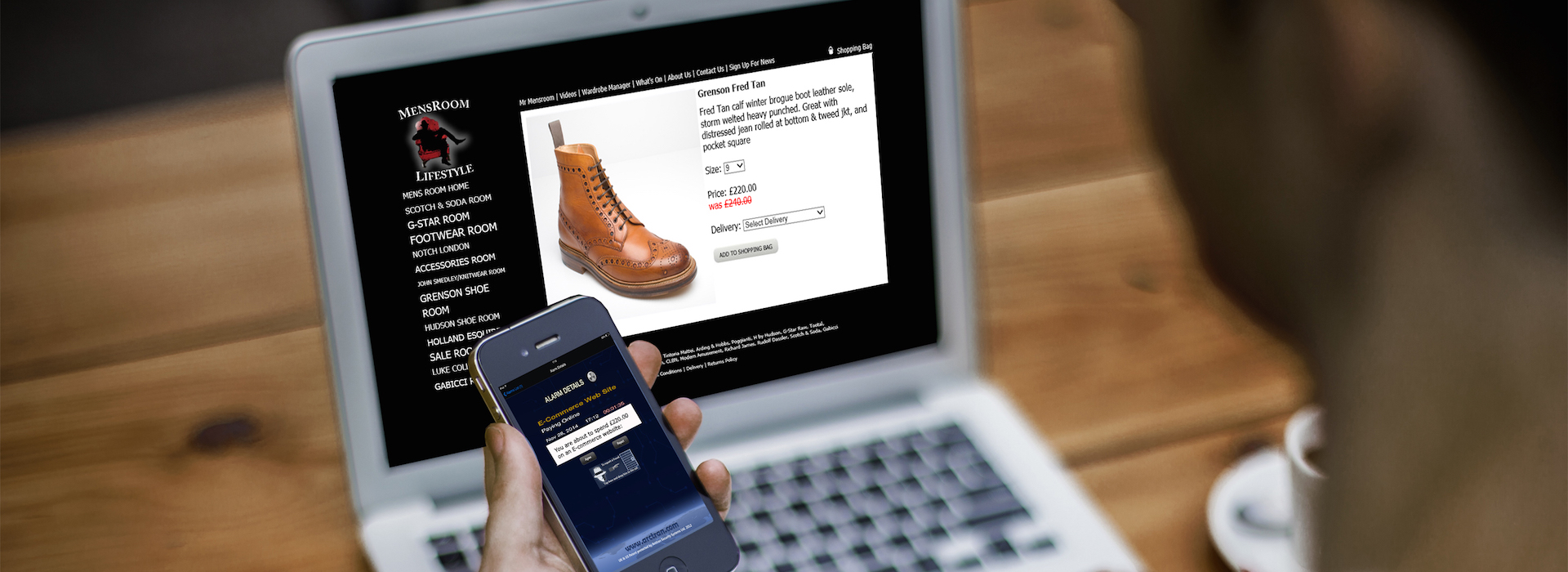
Arctran is a cyber-security system that gives the end-user full control over the final decision made in any electronic environment. Arctran detects any intruder intervention and obtains proof of transaction thereby allowing businesses to increase user confidence.
Secure
End-to-end encrypted communication without any privacy concerns.
Interactive
Providing real-time authorisation and control of sensitive activities.
General Purpose
Not limited to a particular use-case or scenario. Business agnostic.
User Friendly
Just read and tap. A single action to accept, reject or denounce.
Cooperative
Allowing multiple users to participate in the process when required.
Flexible
Supporting auto-acceptable requests through a versatile rules engine.